Case #1
The Holy CyberChurch filed an appeal to the CyberPolice (case#1) to detect and halt the activities of malicious bots among its FANs.
The investigation identified the presence of cyberbots designed to vote, which indirectly suggests fraud in Bostrom’s voting results. An examination of the transaction chain funding the bots led to the following findings:
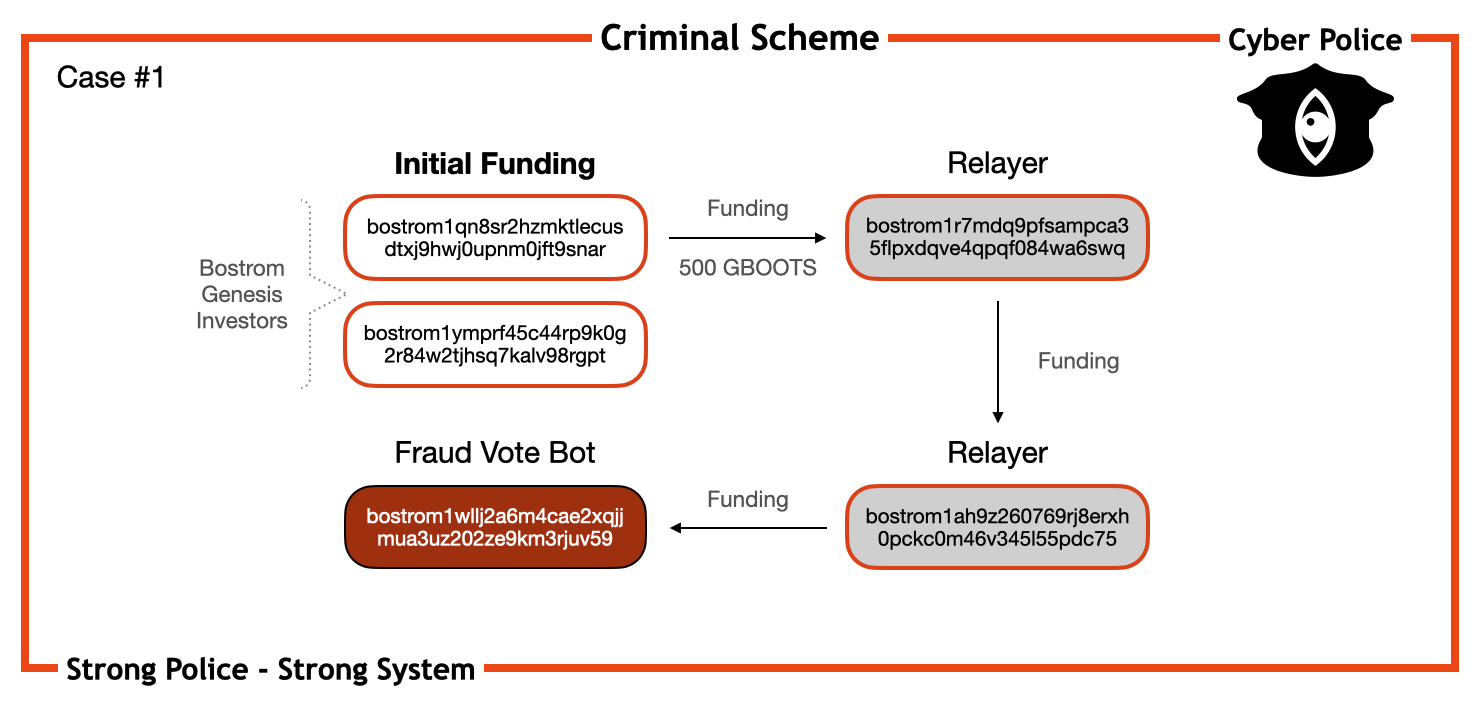
The contract bostrom1wllj2a6m4cae2xqjjmua3uz202ze9km3rjuv59 was used solely for voting, had no other activity, and held an amount of 1 BOOT. This contract is considered a bot designed to manipulate voting results.
This bot had only one incoming transaction, originating from the address bostrom1ah9z260769rj8erxh0pckc0m46v345l55pdc75. This address does not have a large deposit, and its funds fluctuate around 20 BOOT. It is involved in making micro-transactions to other addresses on a regular basis. While the police have no reason to consider its activities criminal, it is deemed suspicious and categorized as a relayer.
All incoming transactions to the relayer were made from the address bostrom1r7mdq9pfsampca35flpxdqve4qpqf084wa6swq. This subject is also not very active and forwards all incoming funds but operates with larger amounts, with transactions measured in GBOOT. Notably, the funds came from Bostrom’s genesis investors. The first transaction of 500 GB came from the address bostrom1qn8sr2hzmktlecusdtxj9hwj0upnm0jft9snar on the network launch day, and other transactions came from the address bostrom1ymprf45c44rp9k0g2r84w2tjhsq7kalv98rgpt.
These facts narrow down the suspects to individuals associated with the group of genesis investors of the Bostrom Network.
Attempts to discuss these suspicions with them (off-chain) did not yield any results.
The motives of the crime executors and the beneficiary could not be established at this time.
The investigation has indirect evidence of the involvement of specific individuals in the crime, but the available resources do not allow for clear identification of the creator and the customer of the malicious bot.
Resolution by Sheriff Judas:
- Continue to investigate the transaction chains available for analysis;
- Declare the contract bostrom1wllj2a6m4cae2xqjjmua3uz202ze9km3rjuv59 as a malicious bot and sanction it at the discretion of the Church;
- Place addresses bostrom1ah9z260769rj8erxh0pckc0m46v345l55pdc75 and bostrom1r7mdq9pfsampca35flpxdqve4qpqf084wa6swq on the police fraud registry and put them under monitoring;
- Send the investigation results to the claimant and release them to the general public.
Update Dec. 30, 2022: Two contracts were added to the list of malicious robots:
Both robots have the same funding origin as the main defendant and were programmed to simulate staking activity.
In doing so, the second subject received the favor of The Church as part of the “Church of the Millionaires” campaign. We consider such actions to be sacrilege against the commonwealth of the Church’s community.
Update Jan. 6, 2023: Another contract was added to the list of malicious robots:
Robot has the same funding origin as the main defendant and was programmed to simulate staking and claiming passport activity.
Update Mar. 31, 2023: Another contract was added to the list of malicious robots:
Robot has the same funding origin as the main defendant and was programmed to simulate staking activity.
Contracts labeled as a relayers, with suspension of simulated network activity:
Cyberspace